Application programming interfaces (APIs) have become a critical part of almost every business. APIs are responsible for transferring information between systems within a company or to external companies. For example, when you log in to a website like Google or Facebook, an API processes your login credentials to verify they are correct.
However, given the sensitive data being transferred through APIs, it’s critical to secure them. Increasingly sophisticated attacks occur every year, requiring better security controls and monitoring. In this article, we’ll give you an overview of the vulnerabilities of APIs, which hackers can take advantage of, and we’ll show you how to secure them. We’ll also show you how to monitor APIs and receive security alerts through SolarWinds® Papertrail™.

The Impact on Businesses
API security is critical to businesses because these interfaces often expose sensitive data and expose the organization’s internal infrastructure to misuse. A security breach could mean leaking sensitive customer data or even personally identifying information in healthcare or finance, which is regulated by law. With the advent of Europe’s General Data Protection Regulation (GDPR), the cost of building GDPR-compliant websites and APIs have only grown. An overactive customer or malicious user may make requests that starve other users of resources, which can also have downstream impacts on dependent systems.
Furthermore, implementing and maintaining API security is an exhaustive process. With the advent of scalable architectures like microservices, controlling access to APIs, and the sensitive data they serve has become more cumbersome. API security incurs the additional cost of implementing features or fixing bugs. Another concern for API developers is that they have to commit a considerable part of the product lifecycle to security.
Businesses also need to focus on API security testing, which requires hiring and accumulating the right talent to identify and expose API-related security holes before the application hits production. Businesses should not think about API security as a mere afterthought—they should inculcate the security best practices in the product development process.
API Vulnerabilities
Since APIs can be accessed over the internet just like any other URI with some sensitive data attached to the request, they share the vulnerabilities of any other resource accessible on the internet.
Man-in-the-Middle
A man-in-the-middle attack is a type of cyberattack in which a malicious actor inserts him/herself into a conversation between two parties, impersonates both parties, and gains access to information that the two parties were trying to send to each other.
To mitigate this attack, it is advisable to upgrade to the safer HTTPS protocol through SSL/TLS certificates. A TLS certificate will activate the HTTPS protocol, which is the safer version of HTTP. This allows an encrypted, secure connection between your server and your clients’ computers, keeping all information from prying middlemen.
CSRF Attack
In cross site request forgery attacks, a hacker takes actions, such as transferring money or changing an email address, in an authenticated web application without the user’s knowledge.
The most popular technique for preventing CSRF attacks are server-generated tokens that are embedded in HTML as hidden fields and sent back to the server with each request so the server can validate if that request is coming from an authenticated source.
XSS Attack
Cross site scripting attacks work by injecting a malicious script into the vulnerable application, making the user reveal his or her session cookies.
Properly escaping the data to eliminate the malicious script and validating the user data for any harmful content can prevent these kinds of attacks.
SQL Injection
SQL injection happens when the user, instead of inputting the valid data, inputs a SQL statement that ultimately gets executed on the database. The best defense against these kinds of attacks are the framework-supported, SQL-prepared statements or using named parameters provided by ORM tools like Hibernate.
Distributed Denial of Services
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of internet traffic. DDoS attacks use multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources. The hardest part about this attack is differentiating between the attack and normal traffic, especially when the traffic comes from botnets that look like regular users.
Credential Stuffing
Credential stuffing is defined by the Open Worldwide Application Security Project® (OWASP) as “mass log-in attempts used to verify the validity of stolen username/password pairs.” In a credential stuffing attack bad actors gain access to login credentials from stolen lists or purchase them on the dark web, and then use bots to test log-in credentials against high value websites, such as banks or ecommerce. Credential stuffing is also used against corporate websites to obtain confidential or proprietary information. Since valid credentials are used, it is difficult to identify malicious logins. The best defense against this type of attack is to implement multifactor authentication (MFA).
Securing APIs
Every digitized business needs APIs, whether RESTful, RPC, or any other technology, to let customers manipulate and manage their business-critical data. After the Cambridge Analytica incident at Facebook and the subsequent implementation of the General Data Protection Regulation (GDPR), API security is even more important.
Whether the communication is between service and server, or services and the browser, the services should not just secure the data they are serving but also control who is requesting that data. Nobody wants to make their social data available to strangers.
Always use HTTPS and SSL Certificates
By always using a secured version of HTTP and the correct SSL certificates, we can make sure that that the integrity of all data exchanges between a client and a server are encrypted, thus reducing the probability of a man-in-the-middle attack, as discussed above.
Firewall Optimizations
A computer firewall is a software program that prevents unauthorized access to or from a private network. And a comprehensive firewall optimization ensures that the unused and overly permissive rules are revoked. The optimization might require analyzing the firewall rules and other network objects for their usage on various service and API workloads.
Authentication and Authorization of Public Clients
Authentication and authorization of clients can help protect the API from misuse. A proven protocol is OAuth 2.0, which enables a third-party application to obtain limited access to an API. It works either on behalf of a resource owner by orchestrating an approval interaction between the resource owner and the API, or by allowing the third-party application to obtain access on its own behalf. If the client to the APIs is a mobile app or browser-based application, you may also consider using third-party authentication via Google, Facebook etc.
IP Whitelisting
IP whitelisting is a security feature that limits access to trusted users or components. IP whitelisting allows you to create lists of trusted IP addresses or IP ranges from which APIs can be accessed.
Rate Limiting
This is another security feature that relies on limiting the number of calls the client can make in a particular time frame. This prevents the APIs from getting overwhelmed by curious clients and helps prevent denial of service attacks.
Access Logs
For any application hosted on the cloud, access logs are an important piece of anomaly detection. They allow operators to zero in on the nature of attack, its possible origin, and to take precautionary measures.
Server Security Logs
Security logs contain the security-related activity as specified in the application audit policy. They are an important tool for administrators, allowing them to detect and investigate the attempted and unauthorized activities.
Analyzing Access and Security Logs in Papertrail
Application logs contain very important product usage data, but in a globally accessible app, these logs are so huge it is impossible for a team to wade through them all. Papertrail makes it easy for one person to make sense of these logs by parsing the logs into tokens and presenting the product usage in an easy-to-use, graphical way. By integrating Papertrail in your application you can track possible vulnerabilities.
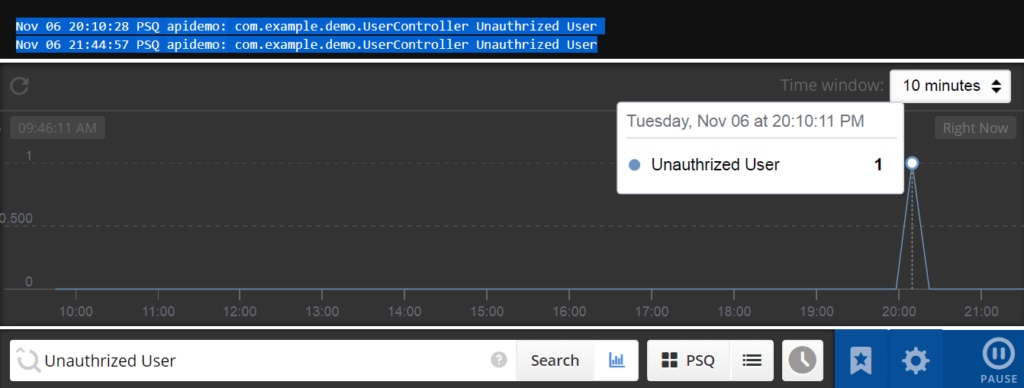
Earlier we described how one of the key approaches to securing API is authentication and authorization. Below we have created a test API with authentication. We have added Papertrail to log the information when an unauthorized user tries to access data.
@RequestMapping("/auth")
public LoginResponse authUser(@RequestHeader(value = "authToken") String authToken) {
LoginResponse response = new LoginResponse();
if (!Constant.authTken.equalsIgnoreCase(authToken)) {
response.setErrorCode(Constant.INVALID_TOKEN_CODE + "");
response.setErrorMsg(Constant.INVALID_TOKEN_MSG);
LOGGER.info(“Unauthrized User”);
return response;
}
User user = new User();
user.setName("Test User");
user.setAge("25");
response.setStatus(true);
response.setErrorCode("200");
response.setErrorMsg("Success");
response.setUserDetail(user);
return response;
}
In the example above, we have added a section to catch those users who are unauthorized. We then execute `LOGGER.info(“Unauthorized User”)` to track the attempt in Papertrail.
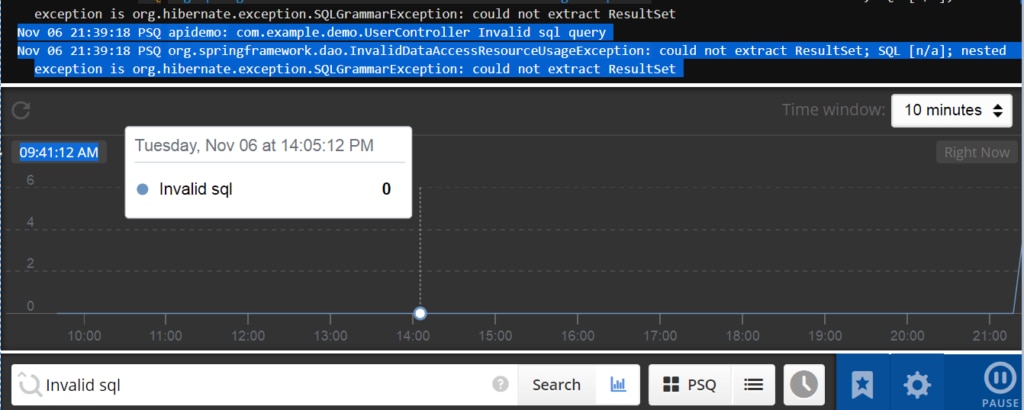
You can track SQL injection vulnerabilities when a user, instead of inputting the valid data, inputs a SQL statement that ultimately gets executed on the database. For example:
@PostMapping("/addUser")
public GenericResponse createQuestion(@Valid @RequestBody User request) {
GenericResponse response = new GenericResponse();
try {
UserEntity entity = new UserEntity();
entity.setAge(request.getAge());
entity.setName(request.getName());
repository.save(entity);
} catch (Exception e) {
LOGGER.error("Invalid sql query", e);
}
return response;
}
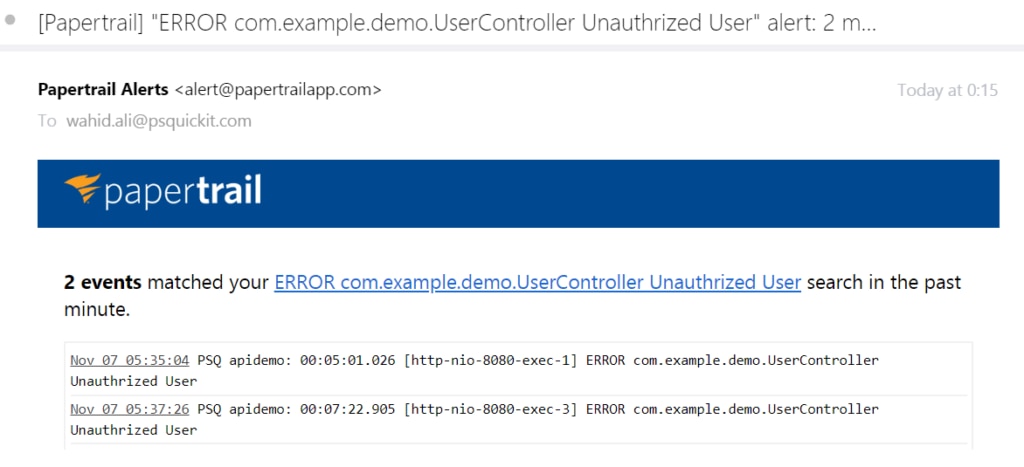
You can also create alerts to notify you when there is an attack, such as a spike in error messages, in the system. You just need to set the search term. You can get the alerts on various endpoints like email, Slack, Hipchat, and more. Now your team will know immediately when there is a problem and can respond quickly.
Conclusion
API security is critical, but SolarWinds Papertrail provides a solution: It gives meaningful insight into application security by offering centralized log management. Papertrail easily integrates with major modern application technology stacks and gives insights into which part of the application is under possible attack. Papertrail helps create alerts on logs that are monitored, giving infrastructure admins enough time to mitigate an attack. Even after an attack, Papertrail gives a forensic view of the application usage behavior, which in turn provides more insights, helping you avert future attacks. Sign up for a free trial of Papertrail today.